NOTE: If you aren’t interested in reading my amazingly-described prose, and just want to know how to keep yourself secure, skip to the bottom of the post. I don’t know why anyone would want to do this, but I felt I should include this notice for completeness.
 Very true.
Very true.I am currently working with Silent Circle, and, as a security company, people count on us to safeguard their privacy, and I like to think we’re doing a pretty good job of it (I was actually surprised at how often far-fetched security edge cases came up in our meetings when I joined). However, most security in the world, where people are involved, rests with successfully verifying that the person to whom you are giving access to the account is actually who they say they are.
That’s usually achieved with a password, which only works if the only person who knows it is the person who owns the account. This requires both parties to take precautions not to reveal it, and we do our best. This post is about how you can do your best.
What’s a good password?
You can’t choose a good password if you don’t know what “good” means. “Good”, in the context of passwords, is pretty much defined as “one that will be difficult to discover”, for any method of discovery (and there are a lot of those). Therefore, to know what a good password is, you need to know how people go about discovering passwords. Here are a few methods:
Rubber-hose cryptanalysis
This is usually the simplest and best way to get a password from a high-value target: Beat them with a rubber hose until they tell you the password.
How to protect against it: This method is very hard to protect against, but, luckily, it is not a big concern to the average user.
Shoulder surfing
Another good way to discover someone’s password: Look over their shoulder while they are typing it.
How to protect against it: Don’t let people look at your screen or keyboard while you are entering passwords.
Stealing a provider’s password database
Bad people have been known to break into service providers’ servers (e.g. our servers) and steal the entire password database. Hopefully, the passwords are stored in a format that is not easily reversed, but not many providers are that careful (we are, so we have that covered for you). They are usually stored in some sort of obfuscated format, so the attacker can’t read them directly, but most providers use a weak format that allows attackers to try billions of passwords per second until they find what the actual password was. Good formats only allow 2-3 password attempts per second.
How to protect against it: Make sure your provider stores passwords securely. You usually can’t, so, do the next best thing: pick a password that is hard to brute force (more on this later).
Outright malicious providers
 Don't fall for this.
Don't fall for this.It’s worth keeping in mind that, when you enter your password on some service, they obviously know your password. If you’re using an untrustworthy service, they might just be harvesting emails and selling them, using them for illegal activities, etc.
How to protect against it: Always use one password per service, and exercise caution and common sense when it comes to sharing passwords with services. There are ways to use one password per service without having to remember them all, using programs called password managers. Such programs are SuperGenPass (it generates new, secure passwords based on a master password and the domain and doesn’t need a password file), KeePassX (encrypts and stores your passwords and other information, you can put the file in Dropbox as long as you pick a good master password), 1password (I haven’t used this, but it seems popular), etc. Make sure you use one of the above services, I like SuperGenPass because you can use it anywhere without needing to have anything other than your master password and it has support for websites, phones, etc.
Key loggers/viruses
There are various malicious programs that record everything you type and send the data back to their operators. They usually scan them for credit card numbers (although those aren’t very useful), bank passwords (much more useful), and other valuable pieces information they can use or sell.
How to protect against it: Make sure your computer is clean, don’t run programs whose purpose you don’t know, and don’t run programs from untrusted sources. It is fairly hard to protect against this, as you have highly trained professionals on one end and casual users on the other, but you should definitely exercise caution in anything that runs on your computer, and run nothing from sketchy websites or other untrusted sources (yes, I do mean porn/gambling/piracy websites, among others).
Picking a good password
 Not a good password.
Not a good password.Now that you know some of the typical ways to get your password (and how to protect from them), let’s move on to more details. From the above, it should be clear that a good password has two properties: It is easy to remember, and it is hard for others to guess. Completely random passwords are bad for the former but good for the latter. The word “password” is good for the former but bad for the latter. Ideally, you will want to strike a balance between the two.
If you’re more afraid of online criminals than that someone will break into your house and steal your bank password, you can write it down and put it somewhere safe. However, as you saw above, picking a single password for everything is risky, as someone who steals one from one service can use it to access all your other accounts (as above, make sure you always use different, secure passwords per service). Use one of the methods recommended above to generate hard-to-guess passwords so you’ll only need to remember one master password.
At this point, you probably have no idea what “hard to guess” means, maybe a password like “hell0!” comes to mind. That is a terrible password, because “guess” in this context doesn’t mean the same as what it means in plain English. When I say “guess”, I really mean “use brute force to find”. To understand how brute-forcing passwords works, here’s a short overview:
How brute force attacks work
Say someone knows your Google username but wants to discover your password (this goes for any service, by the way, not just Google). The easiest thing for someone to do is to just go to our login page, type in your username and start typing one password after the other. If we assume you only used numbers for your password, they can start trying “1”, “2”, “3”, up to “99999999” until they find it.
You can see how this will take some time, but how it will also eventually lead to someone discovering your password, given enough time. The way to protect against this depends solely on the provider (as long as you don’t use a blindingly obvious password, like the word “password”), as they need to limit invalid login attempts. We already do that, so you’re safe.
Stealing a provider’s passwords and trying to guess the passwords works the exact same way, as they are stored in a format that only allows you to try passwords, but not read them directly, as I said above. This greatly speeds up the guessing attempt, because the attacker doesn’t have to go over the network, and they also completely override any protection the provider may offer, as they can try as many passwords as they want. This is precisely why it is important for the provider to choose a format that makes it hard for attackers to try many passwords per second.
Thwarting brute-force attacks
The two factors that make for a secure password are variation and length. Obviously, the longer the password is, the longer it will take for someone to try all combinations. The more varied it is, the more characters the attacker will have to try in order to discover it. Knowing this, a password like “hell0!” will look reasonable, but it isn’t, because, even though it includes numbers and special symbols, it is a predictable transformation of a dictionary word, and there exists software to do these transformations automatically.
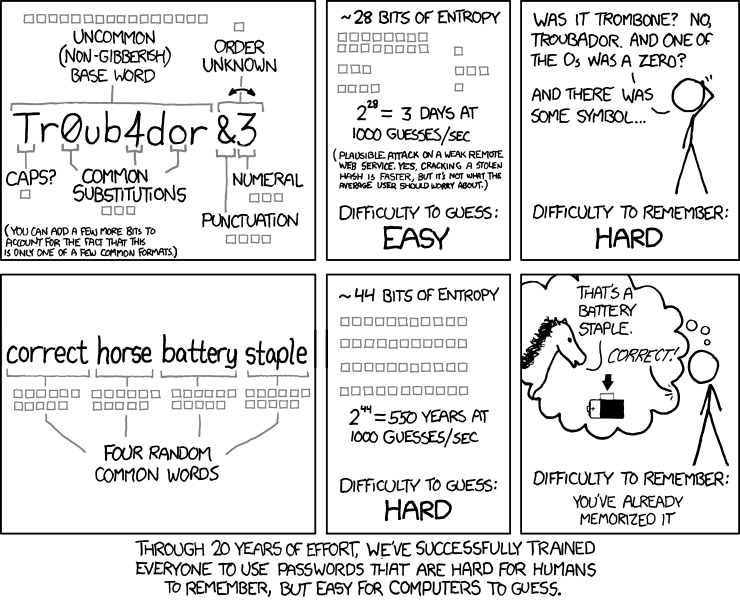
The following well-known XKCD comic illustrates these principles so well, that it has become mandatory content for any post on security:
Without boring you with lengthy explanations on entropy and the like (for technical details on entropy, Dropbox has a good post), extra characters and weird characters in passwords are good, as long as they are unpredictable. Humans are really bad at being unpredictable, but here are some guidelines:
- It’s like the old joke with the two hunters and the bear: In the race for secure passwords, you don’t have to outrun the attacker, you only have to outrun the other users. If your password is more complicated/different enough from what people are usually using, you have an advantage.
- Longer is generally better, at the moment, as most people don’t use very long passwords, and attackers won’t expect them. Steve Gibson’s “Haystack” page has more information on this. If everyone starts using long passphrases composed entirely of words, though, passwords with special characters in them will have an advantage, even if they’re shorter.
- Use one password per service, and use a good password manager to help you keep track of them. This is very important.
- The more random the password, the better it is. This is true always.
- What you think is random, isn’t. This is also true always.
- It is good to pick a method of transforming a common phrase back and forth, just to make it more complicated. This is a good example, but it would also be good to make up your own method based on those guidelines, as the benefit of it is that it is not well-known.
Two-factor authentication
 A 2-factor device.
A 2-factor device.Fortunately, more and more services these days are implementing something called two-factor authentication. Two-factor authentication is a way of using something in addition to your password to identify you, for example a small device that generates numbers (your bank may have one of those), or an app on your phone that you have to enable with your account.
You should always use two-factor authentication. You usually only need to enter a number from your phone once per computer per month, but it will mean that someone who has your password cannot log in to your account at all without also stealing your phone. It is a great security measure, it is very easy to enable and use, and it will help keep your account secure even if your password is somehow stolen.
Best practices summary
 Not just good; best.
Not just good; best.If you don’t want to read everything I wrote above and decide for yourself (you probably shouldn’t, as I probably know better than you), just follow the following recommendation. THIS IS WHAT YOU SHOULD DO:
- Use a different password per service, and use a password manager to store them. Pick one you like, I recommend KeePassX, or SuperGenPass if you don’t want to sync a password file. KeePassX is more flexible because you’ll be able to easily change a password, if needed. Let KeePassX generate long, random passwords for each service you are signing up for.
- Pick a really strong password as your master password, something you can also remember. If random passwords work for you, pick a randomly-generated one that is around 12 characters long and includes lowercase, uppercase, numbers and symbols, if you can remember it. If not, use a passphrase generator (this one looks okay), and generate random words. Generally, 4-5 random words is good, 6 is great if you can remember them.
- Never reveal your master password to anyone, anyone. Write it down and keep it in your safe if you think you might forget it.
- Don’t enter your master password on other people’s computers/phones. If you need to log in on someone else’s computer, use your phone to get the password you used for that service and log in.
- Enable two-factor authentication on anything that supports it. It is totally worth the small hassle, as it will keep you secure even if your password is stolen.
- Exercise common sense. Don’t type your password in untrusted devices, don’t give anyone your password database, don’t log in to untrustworthy sites, and only run programs from trusted sources on your computer. No amount of security can help you if someone steals your password database and master password because you got a computer virus that does that.
Parting words
I hope this post has given you some insight on how passwords protect you and what the most common attempts to compromise them are. By following the best practices in the summary above, you will be much more secure than the average person, but, above all, you need to exercise common sense, as detailed above.
If you’re concerned about your privacy, get a Silent Circle subscription, we take care of everything else so you only have to worry about what was detailed in this post (it is my personal, honest opinion that Silent Circle is very very good about safeguarding your privacy and security, and my recommendation here has nothing to do with my business relationship).